SOLUTIONS TO GUIDE YOUR ENTERPRISE TRANSFORMATION
The Visibility and Support You Need to Manage Growth
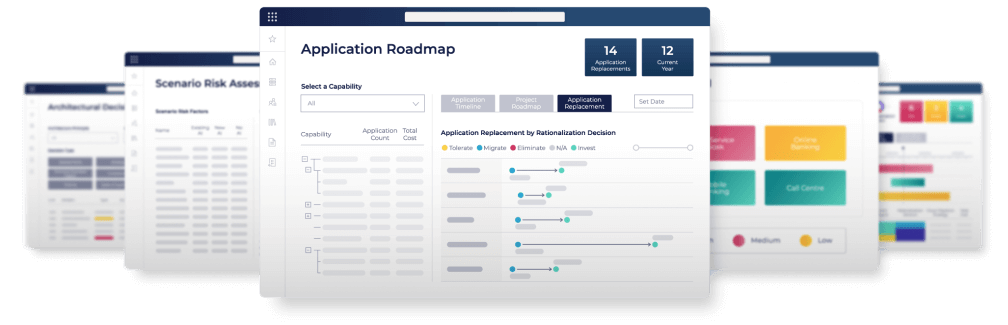
WITH YOU EVERY STEP OF YOUR DIGITAL JOURNEY
Our business-centric platform creates a holistic view of your applications, systems, and data, so you can accelerate decision-making, reduce spend, mitigate risks, and stay resilient in the face of disruption.
ENABLING BUSINESS RESILIENCE
We help solve the challenges facing your business
We understand there are three macro-drivers for change impacting your business:
A decade of disruption
This decade has seen unprecedented disruption, with multiple major disruptors occurring simultaneously. A global pandemic, Brexit, supply chain issues, the Ukraine War, and a pending recession, all contribute towards business uncertainty.
A lack of visibility into business processes
Businesses need to grow, but a lack of visibility into what you own, and your business processes, creates complexity and makes it difficult to align strategy with new integrations and technology.
Meeting ESG requirements
ESG is becoming business critical, and while reorganisation initiatives to improve efficiency are happening, these are often decentralised and difficult to manage.
Our expertise
Helping you scale capabilities

Enterprise Architecture
Equip Enterprise Architecture teams with the powerful analysis tools and data-driven insights necessary to align business strategy with technology initiatives, accelerate decision making and guide strategic transformation.

Strategic Planning
Establish a clear vision with a range of out of the box strategic planning capabilities and identify the business capabilities, processes, and technologies needed to achieve your strategic goals.
Business Process Analysis
Streamline and optimize your business processes with powerful modelling and analysis capabilities. Gain valuable insights, identify bottlenecks, and drive efficiency to achieve your business goals faster and smarter.

IT Portfolio Management
Enhance your organization’s ability to make informed decisions about technology investments with a centralized view of IT assets, associated costs, and alignment with business goals.
OrbusInfinity
A platform for collaboration across your business

OrbusInfinity provides a ‘North Star’ for transformation teams and executives to confidently manage Enterprise Transformations.
It enables architecture teams to collaborate with a wide range of business stakeholders to generate a Digital Blueprint of the Enterprise, enabling exceptional strategic decisions based on a unified view of the business, now and in the future.
SUPPORT ACROSS THE ORGANIZATION
Who we help
"For me, OrbusInfinity has become a part of my mindset in my daily work as an IT architect. It is a part of my tool belt, presenting us with opportunities to solve problems in new and better ways. The work we did around the robotic process automation initiative is an example of where OrbusInfinity shines."
Thomas Pedersen
IT Architect
GF Forsikring
OrbusInfinity serves as a powerful tool for Enterprise Architects, fostering a strategic alignment between IT and business aims. By delivering critical insights, it supports in shaping digital transformation initiatives and developing comprehensive solution strategies.
To elaborate, some of the key benefits for Enterprise Architects include:
- Align IT strategy with business goals.
- Deliver insights.
- Drive digital transformation initiatives.
- Formulate solution strategies.
80%
time saved creating architecture artefacts
70%
reduction in onboarding times of new starters
"It’s the flexibility to be able to design whatever we want. There are no limitations in OrbusInfinity. We can express whatever we want and even do it quickly. We decide we want to make a change, then we can just throw it in the tool. OrbusInfinity is really fast"
IT SPECIALIST
US Bank
OrbusInfinity acts as a powerful ally for Engineering, IT and Operations Teams. It offers a unified platform that streamlines operations, optimizes workflows, and facilitates efficient communication, leading to more coordinated actions. Moreover, by delivering real-time data, it empowers these teams to make informed decisions swiftly.
To delve deeper, some specific benefits for Engineering, IT and Operations Teams are:
- Streamlined operations and workflow optimization.
- Enhanced team collaboration and coordination.
- Access to real-time, actionable data.
- Swift and informed decision-making capabilities.
50%
50% reduction in time spent on resiliency analysis work
95%
reduction in strategic decision analysis
"Our solution architects are having more strategic conversations with portfolio leaders based on the data, and it is really bringing a lot more value."
CTO
leading Construction COMPANY
For C-level executives, OrbusInfinity offers a comprehensive, high-level view of the organization’s operations and strategy. It provides the necessary insights to inform strategic decisions and drive the organization towards its overarching goals. Additionally, the platform aids in identifying growth opportunities and risk management.
To specify, C-level executives can reap benefits such as:
- Comprehensive insights for strategic decision-making.
- Alignment of operations with organizational objectives.
- Identification of growth opportunities.
- Effective risk identification and management.
394%
ROI in 3 years
10 months
payback time
Start your journey
Your journey to resilience with Orbus
From banking, government, healthcare, technology, and everything in-between, we provide a platform for business-centric technology strategy that helps you drive results.
With Orbus, you’ll have access to a team of experts, a dedicated SaaS platform, and a suite of tools to help you uncover insights, inspire ideas, and execute your strategy to make a positive impact on the future of your business.
- Visualize your business process
- Align tech capabilities
- Foster collaboration
- Ensure resilience
- Drive meaningful, continuous change
"Managing technical debt isn’t just about cost – it’s about preventing unseen risks before they become issues. Like insurance, it protects your organization from future challenges you might not even anticipate."
OrbusInfinity Costumer
Enterprise Architect