Guide and Accelerate Strategic Transformation
Enterprise Architecture
OUT-OF-THE-BOX TOOLKITS FOR EA TEAMS
Equip enterprise architecture teams with the powerful analysis tools and data-driven insights necessary to align business strategy with technology initiatives, accelerate decision making and guide strategic transformation.
| COMMON CHALLENGES | ENTERPRISE ARCHITECTURE SOLUTION OUTCOMES |
|---|---|
Siloed, ungoverned and duplicated information | A central source of truth for enterprise data |
No common language for Enterprise Architecture | Universally understood architectural concepts and terminology |
EA Teams slow to demonstrate value to the business | Fast delivery of EA artifacts and actionable insights |
Clouded view of complex business and IT landscapes | Visibility, traceability and clarity across business and IT |
Unknown impact of changes delays decision-making | Clear impact of change supporting faster decisions |
BUSINESS-CENTRIC ENTERPRISE ARCHITECTURE
Make enterprise architecture an internal management consultancy for the business

Unify and govern enterprise data
A central source of truth to govern data and provide a holistic view of your business and technology architectures
- Integrate and sync with a range of existing data sources
- Crowd-source data from SMEs across the organisation
- Govern business and IT data in central repository

Partner with the business
Foster a close partnership between Enterprise Architecture and the business to deliver successful outcomes
- Engage business stakeholders in the tools they use daily
- Source information easily to co-create architecture
- Communicate and collaborate across business functions

Standardize and automate outputs
Ensure stakeholders align to a common language and enhance the productivity of the Enterprise Architecture team
- Leverage out of the box support for common Enterprise Architecture frameworks
- Automate time-consuming and repetitive tasks for architects
- Accelerate time to value with pre-packaged toolkits and reports

Enable intelligent decisions
Auto-generate data-driven reports and visualisations that drive informed decision-making
- Surface dynamic reports with clearly actionable insights
- Highlight the impact and ripple-effect of change
- Provide the answers to guide strategic transformation

2024 Gartner Magic Quadrant Leader for EA Tools
Orbus Software leads in 'Ability to Execute' and 'Completeness of Vision' for the third consecutive year.

8 Steps to Start a High-Impact EA Practice
Discover the key strategies and expert insights from Gartner to establish a high-impact enterprise architecture practice
ENTERPRISE ARCHITECTURE USE CASES
Benefit from tailored toolkits and guidance for common Enterprise Architecture use cases
Application Architecture
Maintain an up to date, comprehensive view of you application landscape and interdependencies
- Import existing application data from lists in Excel or ITSM systems such as ServiceNow to create a central inventory
- Enrich you application data by sourcing data from application owners and other stakeholder across the organisation
- Map interdependencies with other components such as business capabilities, processes and technologies
- Generate application architecture diagrams and socialise with key stakeholders for feedback and analysis
- Provide a range of application insights to support portfolio management and Roadmapping activities
Technology Architecture
Build a centralised view of your technology ecosystem aligned to application and business goals
- Populate your repository with technologies sourced from existing catalogues in Excel or ITSM system such as ServiceNow
- Easily map interdependencies with other organisational components such as applications, processes and data
- Enrich your technology architecture with data sourced from stakeholders and lifecycle management systems such as Flexera
- Provide actionable insights to support technology portfolio management, lifecycle management and roadmapping
Solution Architecture
Design cross-domain architectural solutions to address specific organizational requirements
- Collaborate with business stakeholders to capture business requirements, goals and constraints
- Analyse the different business, data, and technology components required to achieve specific organisational outcomes
- Model the required solution architectures and auto-generate Solution Design Documents and other outputs
- Share Solution Architecture outputs with technology teams and DevOps to guide and de-risk implementation
Business Architecture
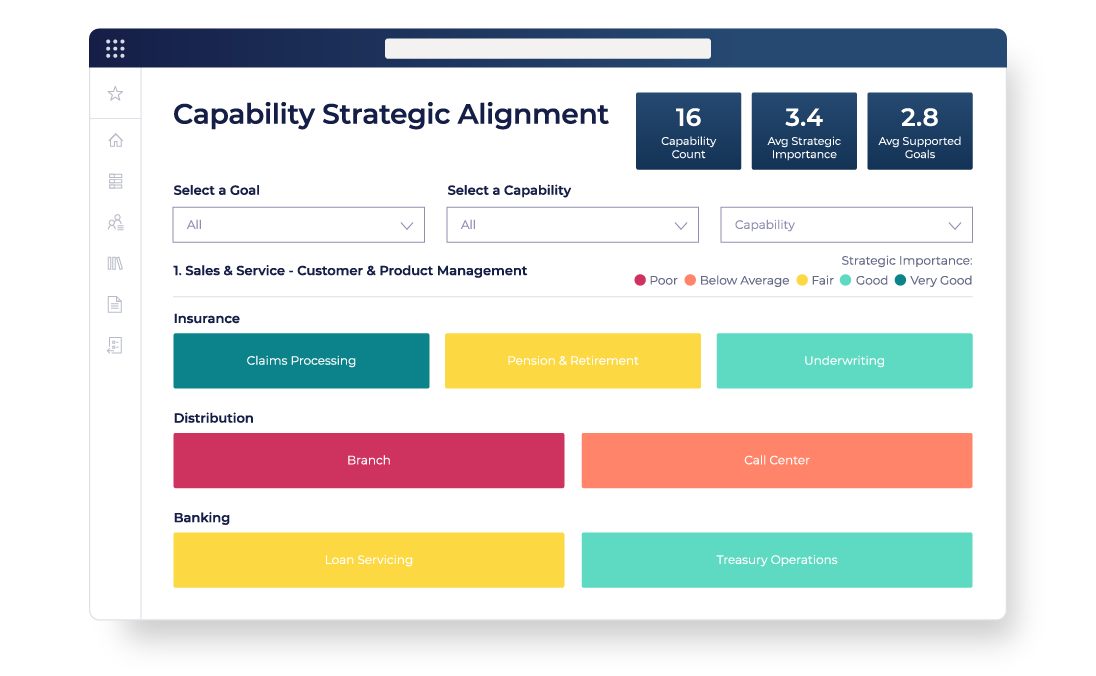
Move beyond ‘IT architecture’ to focus on business strategy and outcomes
- Engage key stakeholders from different business units to capture strategies and desired business outcomes
- Model the current-state business architecture, including goals, capabilities, org structures, processes and information flows
- Co-create the future-state business architecture required to support the organisation’s goals and objectives
- Develop the BA roadmap, outlining the steps and activities required to transition from the current-state to the future-vision
- Enable better decision-making, strategy alignment, and operational optimization across the business.
Data Architecture
Define the blueprint for data assets required to support your organisational goals
- Create data models defining the structure, data and attributes of data entities within your organisation
- Define integration principles which ensuring data consistency, quality, and accuracy across different systems.
- Establishes data governance frameworks, policies, and standards that guide your organization's data-related practices.
- Ensure your data landscape is supported by and aligns to your technology infrastructure, now and in the future
Kick-start your transformation
Enterprise Architecture Use Cases
Enterprise Architecture Success Story
How OrbusInfinity aligned perfectly with Scottish Water
Scottish Water re-selects Orbus as their Enterprise Architecture tool

enterprise architecture RESOURCES
Find resources that can help your digital future
OUR CUSTOMERS HAVE SPOKEN


